
Calyptix Security last week sent out a technical advisory warning its community of an uptick in Qakbot and Emotet infections. In light of the increase in phishing campaigns in recent weeks, it’s a good idea to review best practices. Help prevent compromise from phishing campaigns with the top strategies addressed in this article.
Calyptix’s N’dia Thomas, Cyber Threat and Incident Response Analyst, released an advisory March 10 warning of “an uptick in the volume of outbound botnet and command and control server (C2) activity as well as Emotet and Qakbot infections in the past few weeks. This activity correlates to updated malicious email campaigns detected in the past two months.”
Both Emotet and Qakbot have been around for years. Yet threat actors continuously update malware to improve efficiency. Take the case of Qakbot, aka Qbot Quakbot, Pinkslipbot. The malware has been known since 2007. Yet in October 2021, the DFIR Report found, it now takes the malware only 30 minutes to steal credentials.
Emotet and Qakbot email campaigns use social engineering to trick users into opening a malicious link or macro-enabled document that leads to the compromise of the device, and possibly even the network as the malware spreads laterally.
Qakbot is a modular banking Trojan that steals data and credentials from infected devices. It initially accesses systems through email campaigns used to deliver a malicious link, an embedded image, or a malicious attachment – typically a macro-enabled document.
When the macro is enabled, the Qakbot loader is saved to the disk, and infection begins by injecting into processes and elevating itself to have SYSTEM privileges. It can evade detection by modifying the Windows Defender Exclusions list to exclude its process.
Within thirty minutes, Qakbot can collect and exfiltrate credentials from memory, browser data, and emails from Outlook. Within 50 minutes, it can move laterally to other workstations in the network, repeating the infection process – and in some cases, can drop Cobalt Strike that leads to ransomware.
Emotet, first observed in 2014, is another modular Trojan. It is primarily used to distribute other malware such as ransomware, TrickBot, and other banking Trojans. It is similar to Qakbot in that it utilizes email campaigns to deliver a malicious link or attachment that convinces users to enable macros to start infection.
Like Qakbot, Emotet email campaigns use stolen reply-chain emails. However, Emotet also hijacks existing email chains and take advantage of current events such as COVID-19 and the Russia/Ukraine conflict to lure recipients to download and open malicious attachments.
Emotet differs from Qakbot in that it can go through the contact list of a user’s email client and send itself to their coworkers, clients, family, and friends. The recipients of such emails are more likely to trust the email since they know the sender. It has multiple methods to maintain persistence and avoid detection and can spread laterally through brute-force attacks.
Calyptix has deployed Community Shield on AccessEnforcer (version 5.0.3), which includes multiple threat feeds consisting of IP addresses for known C2 servers and botnets to block inbound and outbound traffic.
Any outbound alerts generated by these known IPs are detailed on an Outbound Activity Notification Report sent to our users’ designated alert contact via email.
Additionally, we have recently implemented a new alerting system to notify us of any attempts to connect to these known IPs within 30 minutes to facilitate faster notification of potential infections.
Follow these best practices for phishing campaigns to prevent falling victim to these or other similar malware attacks.
It will also help to educate users to be aware of the social engineering tactics employed by these phishing campaigns. Encourage your users to look out for:
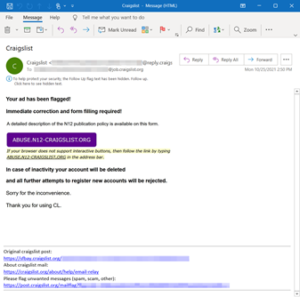
An overall good rule of thumb is to be wary of every link and attachment sent in an email. This is especially true if it came from an external source and you don’t know the sender.
If you receive a suspicious message:
Any MSPs who do receive these types of reports can also let us know. Calyptix works diligently to fortify the online community for all our customers with shared information via Community Shield. Learn more today!